You've seen them embedding YouTube videos, Google Maps, or maybe even interactive forms on websites. Iframes (Inline Frames) are a powerful HTML tool for displaying content from one web page inside another. But this leads to a common question: is it possible to embed any website inside an iframe?
The short answer is FALSE.
While the <iframe> tag itself is simple, security measures built into the web prevent you from arbitrarily embedding any website you choose. This guide explains exactly why, covering:
What iframes are.
The security headers (X-Frame-Options, Content-Security-Policy) that control embedding.
Why these restrictions exist (preventing threats like clickjacking).
How to protect your own site from being framed inappropriately.
When iframes can be used effectively (including tools like Poper).
Understanding iFrames and Embedding
So, you're thinking about using iframes to embed content? Great! They can be really useful for integrating things smoothly. Let's break down what they are and the rules of the road.
What are iFrames?
Think of an iframe (short for Inline Frame) as a window within your webpage that looks into another webpage. It uses a simple HTML tag, <iframe>, where you specify the src (the URL of the page you want to embed).
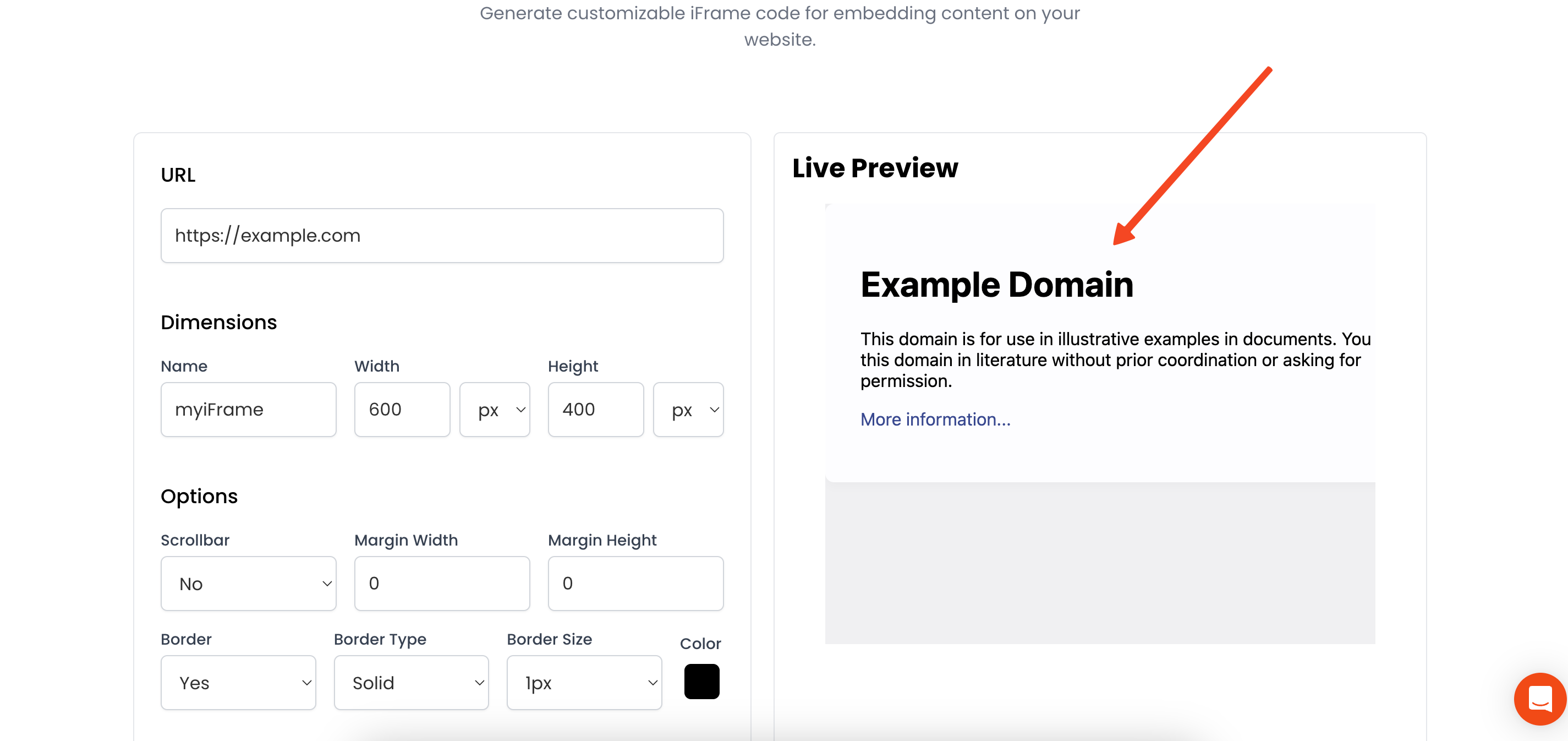
This allows you to display content from another source directly within your own site's layout. It's like putting a picture frame on your wall, but instead of a picture, it holds a whole other webpage.
Are browser variables shared across iframes?
This is a key point for security. Generally, no, browser variables (like those set by JavaScript) are not shared between the parent page and the iframe if they are from different origins (different domains, protocols, or ports).
This separation is crucial; it prevents a page embedded in an iframe from potentially accessing sensitive information or manipulating the parent page, and vice-versa. Imagine the security risks if any embedded ad could just read your website's internal data!
If the iframe content comes from the same origin as the parent page, there's more potential for interaction, but that's a less common scenario when embedding external websites. For embedding third-party content, assume isolation.
What is X-Frame-Options? And how does it work?
Now, here's where we get to the heart of embedding any website. X-Frame-Options is an HTTP response header that a website can send back to the browser.
It essentially tells the browser whether it's okay for the page to be displayed inside an <frame>, <iframe>, <embed>, or <object>. It's a security measure designed primarily to prevent "clickjacking" attacks.
There are three main settings for X-Frame-Options:
DENY: This completely prevents the page from being loaded inside any frame, anywhere.SAMEORIGIN: This allows the page to be framed, but only by pages from the exact same origin (domain).ALLOW-FROM uri: (This one is a bit older and less consistently supported) It lets you specify a particular URL that is allowed to frame the page.
If a website sends X-Frame-Options: DENY or X-Frame-Options: SAMEORIGIN (and you're trying to embed it from a different origin), the browser simply won't display it in your iframe.
You'll usually just see a blank space or a browser error message in the frame. There's also a newer, more flexible header called Content-Security-Policy with a frame-ancestors directive that achieves similar goals.
So, True or False: It is possible to embed any website inside iframes?
Based on what we just discussed about X-Frame-Options, the answer is false. You can only embed websites that explicitly allow themselves to be embedded, either by not sending the X-Frame-Options or Content-Security-Policy: frame-ancestors headers, or by setting them in a way that permits embedding (like SAMEORIGIN if you are on the same domain, or sometimes ALLOW-FROM).
Many major websites (like Google, Facebook, and many banks) set these headers strictly to prevent embedding for security reasons.
Can hackers mimic a website by using your website as an iframe and how to prevent it?
Yes, this is a real threat called "clickjacking" or "UI redressing." A hacker could create their own malicious page and embed your legitimate website within an invisible or cleverly disguised iframe.
They might then overlay fake buttons or links on top of your actual buttons within the iframe.
A user visiting the hacker's site might think they are clicking something harmless on the hacker's page, but they are actually clicking a button (like "Transfer Funds" or "Grant Permissions") on your invisible, framed website.
The primary way you prevent your website from being misused like this is by using the X-Frame-Options header (setting it to DENY or SAMEORIGIN) or the Content-Security-Policy: frame-ancestors directive on your own web server.
This tells browsers not to render your site inside an iframe on potentially malicious domains, stopping clickjacking attempts that rely on framing your content.
X-Frame-Options vs. CSP frame-ancestors Quick Comparison
| Feature | X-Frame-Options | Content-Security-Policy: frame-ancestors | Notes |
| Purpose | Prevent clickjacking via framing | Prevent clickjacking via framing | CSP covers many other security aspects too. |
| Directives | DENY, SAMEORIGIN, ALLOW-FROM uri | 'none', 'self', uri(s) | Multiple URIs can be specified in CSP. |
| Flexibility | Limited (e.g., ALLOW-FROM poorly supported) | High (multiple sources, granular control) | CSP is the modern standard. |
| Support | Widespread (older browsers too) | Good (modern browsers) | Browsers often prioritize CSP if both headers are present. |
| Recommendation | Use as fallback | Preferred method | Implement CSP frame-ancestors for robust protection. |
Result: Because many major websites (Google search, Facebook, banks, etc.) send restrictive X-Frame-Options or CSP frame-ancestors headers (like DENY or 'none'), your browser respects their wishes and refuses to display them in your iframe. You'll often see a blank iframe or a browser-specific error message.
The Threat: What is Clickjacking?
Why do websites block embedding? A major reason is to prevent clickjacking (also called UI redressing). Here’s how it works:
A hacker creates a malicious webpage.
They embed your legitimate website (e.g., your webmail, your social media settings page, your online store checkout) into their page using an invisible or cleverly disguised iframe.
They overlay tempting buttons or links on their page (e.g., "Click here to win a prize!") that are perfectly aligned over important buttons within your invisible framed site (e.g., "Delete all emails," "Share my location," "Confirm purchase").
A victim visits the hacker's page and clicks the harmless-looking button.
Because the invisible iframe is underneath, they unknowingly click the button on your website, performing an action they never intended.
Restricting framing via XFO or CSP frame-ancestors is the primary defense against this attack.
Are Browser Variables Shared Across iFrames? (Same-Origin Policy)
Generally, no, especially if the iframe content comes from a different origin (domain, protocol, or port) than the parent page. The Same-Origin Policy is a fundamental browser security mechanism that prevents scripts on one page from accessing data or properties of a page from another origin. This isolation is crucial – you wouldn't want an embedded ad's script to read cookies or data from your main website.
How to Prevent Your Website From Being Maliciously Framed
Just as you can't embed sites that block framing, you should protect your own site from being used in clickjacking attacks. Configure your web server to send one of these headers for all your pages:
Recommended: Content-Security-Policy: frame-ancestors 'self'; (Allows framing only by your own domain)
- Or Content-Security-Policy: frame-ancestors 'none'; (Completely blocks framing)
Or Content-Security-Policy: frame-ancestors 'none'; (Completely blocks framing)
Fallback: X-Frame-Options: SAMEORIGIN
- Or X-Frame-Options: DENY
Or X-Frame-Options: DENY
Implementing these headers is a critical security best practice.
When Can You Use iFrames Effectively?
Iframes are still incredibly useful for embedding content that is designed or permitted to be embedded. Common examples include:
YouTube Videos: YouTube provides specific iframe embed code.
Google Maps: Google Maps offers embeddable iframe code.
Social Media Feeds: Some platforms provide embeddable widgets (often using iframes).
Third-Party Forms & Widgets: Services like payment processors, booking systems, or engagement platforms like Poper often provide code snippets (which might utilize iframes or other embed techniques) to integrate their functionality into your site. Poper's popups, embeds, and widgets are intended to be placed on your website using its provided script and configurations.
In these cases, the source service either doesn't send restrictive headers or explicitly allows embedding, often because the iframe content is self-contained and doesn't pose the same security risks as embedding an entire interactive website.
Conclusion: Respect the Frame Game
So, true or false: it is possible to embed any website inside iframes? The answer is definitively false due to crucial security headers like X-Frame-Options and Content-Security-Policy: frame-ancestors. These headers protect websites and users from attacks like clickjacking.
While you can't frame just any site, iframes remain essential for integrating permitted third-party content like videos, maps, and specialized widgets such as those provided by platforms like Poper. Always ensure you have permission or are using the official embed method provided by the content source.
Frequently Asked Questions (FAQs) about iFrames and Embedding
How can I check if a website allows itself to be embedded in an iframe?
You can use your browser's Developer Tools (usually F12). Go to the "Network" tab, load the website URL directly, click on the main document request (usually the first one), and look at the "Response Headers" section. Check for X-Frame-Options or Content-Security-Policy headers and their values (DENY, SAMEORIGIN, frame-ancestors 'none', frame-ancestors 'self'). If they are restrictive, you likely can't embed it from a different domain.
Is there any way to force a website into an iframe if it blocks embedding?
No, not from the client-side (your HTML page). Browser security mechanisms enforced via HTTP headers prevent this reliably. Trying to bypass these restrictions often involves server-side proxies, which can be complex, fragile, and may violate the terms of service of the website you're trying to embed.
How do tools like Poper embed content if iframes have restrictions?
Poper embeds its own content (popups, widgets, forms created within the Poper platform) onto your site using a JavaScript snippet you install. This script dynamically adds the necessary HTML (which might sometimes include iframes for specific Poper elements, designed for safe cross-domain communication where needed) to display the campaigns you configure in your Poper dashboard. Poper isn't embedding arbitrary third-party websites; it's delivering its own functionality to your website.
Does using iframes hurt my website's SEO?
Content inside an iframe from a different domain is generally not indexed by search engines as part of your page. Search engines usually understand it's separate content. Therefore, relying heavily on iframes to display your primary content is bad for SEO. However, using iframes for supplementary content like maps, videos, or specific tools (like Poper widgets) is perfectly fine and generally doesn't pose an SEO issue.
What's the difference between embedding and linking?
Linking (<a href="...">) creates a clickable text or image that takes the user away from your page to another URL when clicked. Embedding (<iframe>) displays the content of another URL directly within your current page's layout, without the user navigating away.


